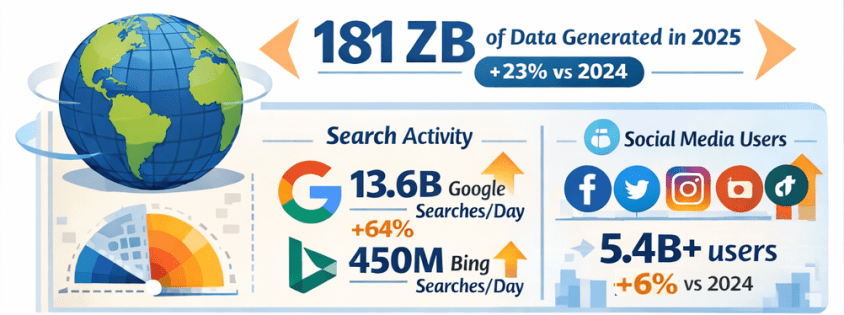
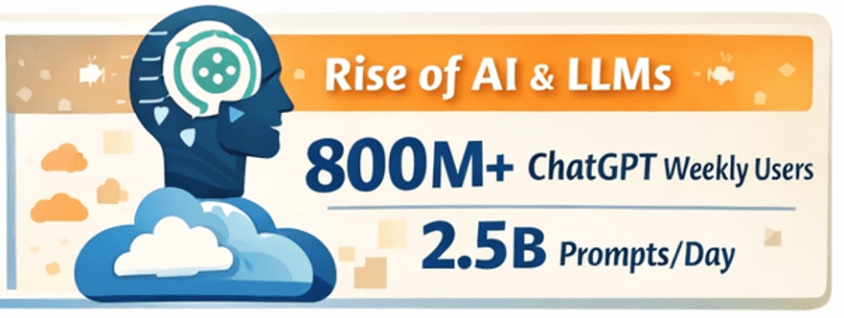
Cybersecurity has always been a race between attackers and defenders. What’s changed is the speed, scale, and sophistication of threats. Cloud computing, remote work, IoT, and AI-generated attacks have dramatically expanded the attack surface—far beyond what human analysts alone can manage.
AI has become a foundational capability in cybersecurity, enabling organizations to detect threats faster, respond automatically, and continuously adapt to new attack patterns.
How AI Is Being Used in Cybersecurity Today
AI is now embedded across nearly every cybersecurity function:
Threat Detection & Anomaly Detection
- Darktrace uses self-learning AI to model “normal” behavior across networks and detect anomalies in real time.
- Vectra AI applies machine learning to identify hidden attacker behaviors in network and identity data.
Endpoint Protection & Malware Detection
- CrowdStrike Falcon uses AI and behavioral analytics to detect malware and fileless attacks on endpoints.
- Microsoft Defender for Endpoint applies ML models trained on trillions of signals to identify emerging threats.
Security Operations (SOC) Automation
- Palo Alto Networks Cortex XSIAM uses AI to correlate alerts, reduce noise, and automate incident response.
- Splunk AI Assistant helps analysts investigate incidents faster using natural language queries.
Phishing & Social Engineering Defense
- Proofpoint and Abnormal Security use AI to analyze email content, sender behavior, and context to stop phishing and business email compromise (BEC).
Identity & Access Security
- Okta and Microsoft Entra ID use AI to detect anomalous login behavior and enforce adaptive authentication.
- AI flags compromised credentials and impossible travel scenarios.
Vulnerability Management
- Tenable and Qualys use AI to prioritize vulnerabilities based on exploit likelihood and business impact rather than raw CVSS scores.
Tools, Technologies, and Forms of AI in Use
Cybersecurity AI blends multiple techniques into layered defenses:
- Machine Learning (Supervised & Unsupervised)
Used for classification (malware vs. benign) and anomaly detection. - Behavioral Analytics
AI models baseline normal user, device, and network behavior to detect deviations. - Natural Language Processing (NLP)
Used to analyze phishing emails, threat intelligence reports, and security logs. - Generative AI & Large Language Models (LLMs)
- Used defensively as SOC copilots, investigation assistants, and policy generators
- Examples: Microsoft Security Copilot, Google Chronicle AI, Palo Alto Cortex Copilot
- Graph AI
Maps relationships between users, devices, identities, and events to identify attack paths. - Security AI Platforms
- Microsoft Security Copilot
- IBM QRadar Advisor with Watson
- Google Chronicle
- AWS GuardDuty
Benefits Organizations Are Realizing
Companies using AI-driven cybersecurity report major advantages:
- Faster Threat Detection (minutes instead of days or weeks)
- Reduced Alert Fatigue through intelligent correlation
- Lower Mean Time to Respond (MTTR)
- Improved Detection of Zero-Day and Unknown Threats
- More Efficient SOC Operations with fewer analysts
- Scalability across hybrid and multi-cloud environments
In a world where attackers automate their attacks, AI is often the only way defenders can keep pace.
Pitfalls and Challenges
Despite its power, AI in cybersecurity comes with real risks:
False Positives and False Confidence
- Poorly trained models can overwhelm teams or miss subtle attacks.
Bias and Blind Spots
- AI trained on incomplete or biased data may fail to detect novel attack patterns or underrepresent certain environments.
Explainability Issues
- Security teams and auditors need to understand why an alert fired—black-box models can erode trust.
AI Used by Attackers
- Generative AI is being used to create more convincing phishing emails, deepfake voice attacks, and automated malware.
Over-Automation Risks
- Fully automated response without human oversight can unintentionally disrupt business operations.
Where AI Is Headed in Cybersecurity
The future of AI in cybersecurity is increasingly autonomous and proactive:
- Autonomous SOCs
AI systems that investigate, triage, and respond to incidents with minimal human intervention. - Predictive Security
Models that anticipate attacks before they occur by analyzing attacker behavior trends. - AI vs. AI Security Battles
Defensive AI systems dynamically adapting to attacker AI in real time. - Deeper Identity-Centric Security
AI focusing more on identity, access patterns, and behavioral trust rather than perimeter defense. - Generative AI as a Security Teammate
Natural language interfaces for investigations, playbooks, compliance, and training.
How Organizations Can Gain an Advantage
To succeed in this fast-changing environment, organizations should:
- Treat AI as a Force Multiplier, Not a Replacement
Human expertise remains essential for context and judgment. - Invest in High-Quality Telemetry
Better data leads to better detection—logs, identity signals, and endpoint visibility matter. - Focus on Explainable and Governed AI
Transparency builds trust with analysts, leadership, and regulators. - Prepare for AI-Powered Attacks
Assume attackers are already using AI—and design defenses accordingly. - Upskill Security Teams
Analysts who understand AI can tune models and use copilots more effectively. - Adopt a Platform Strategy
Integrated AI platforms reduce complexity and improve signal correlation.
Final Thoughts
AI has shifted cybersecurity from a reactive, alert-driven discipline into an adaptive, intelligence-led function. As attackers scale their operations with automation and generative AI, defenders have little choice but to do the same—responsibly and strategically.
In cybersecurity, AI isn’t just improving defense—it’s redefining what defense looks like in the first place.